

jvehent.github.io/modern-webappsec/

 |
Dependency management (supply chain) is a complete dumpster fire |
Modern WebAppSecin seven steps |
|
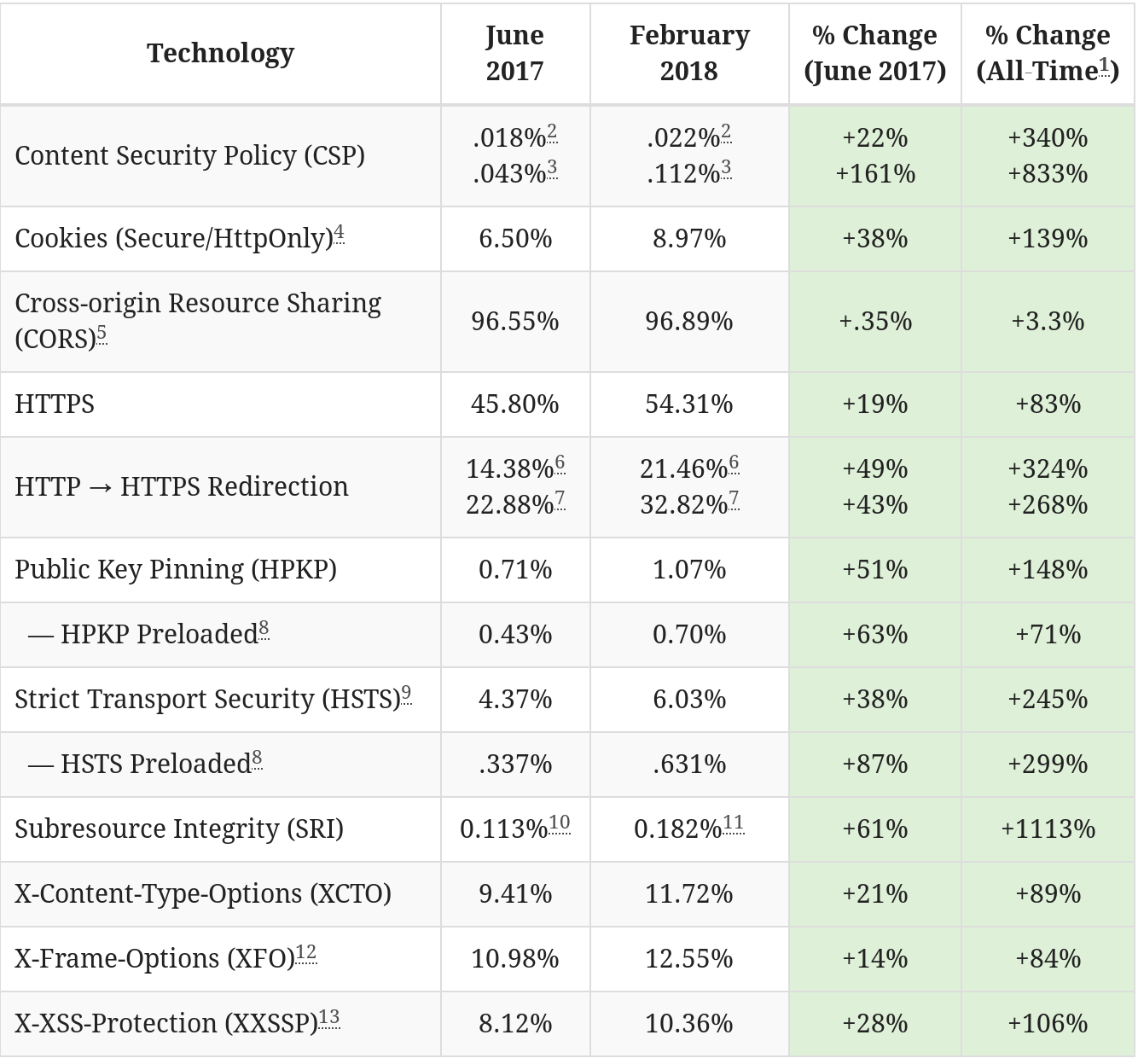
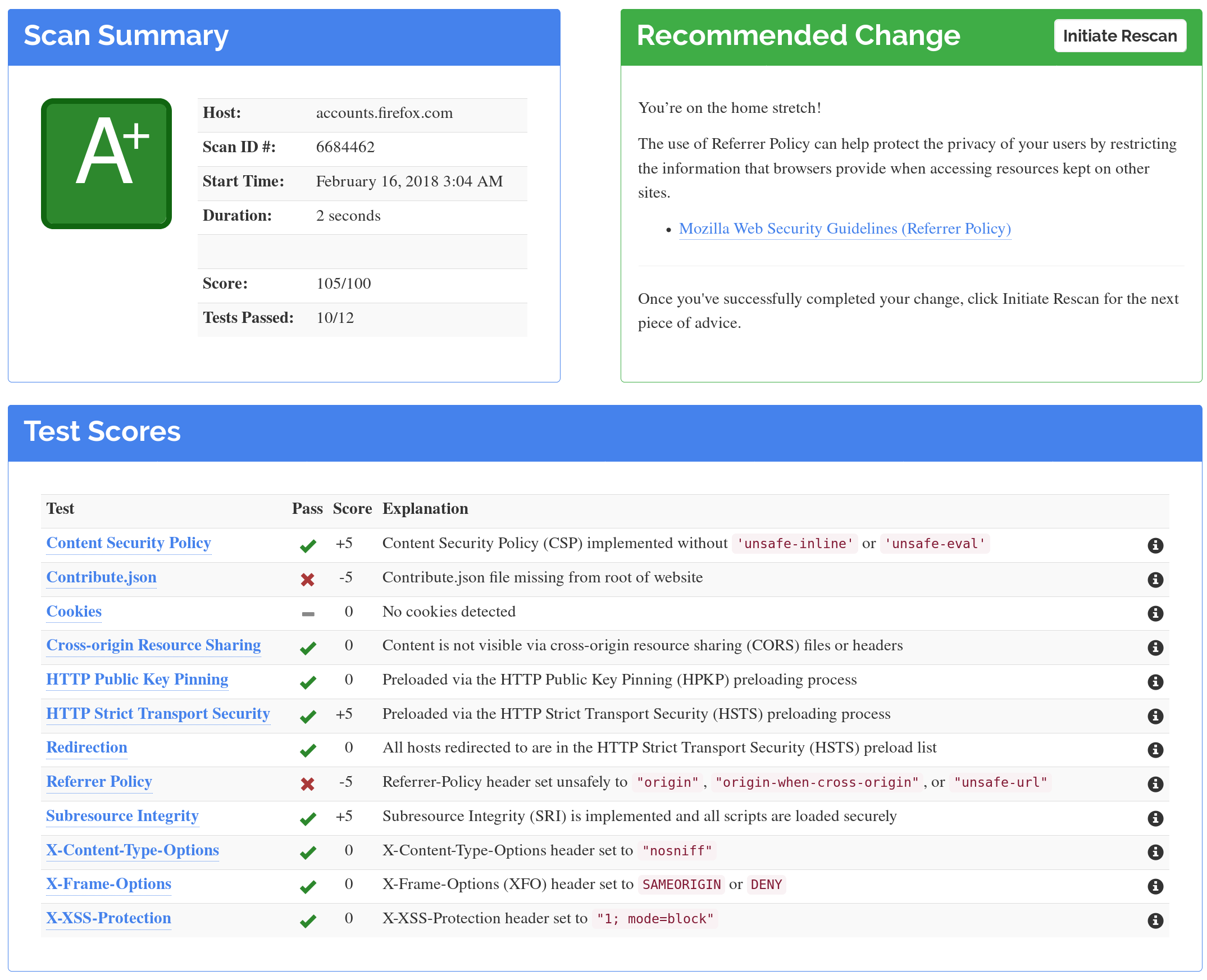
A pre-requisite to any website built today
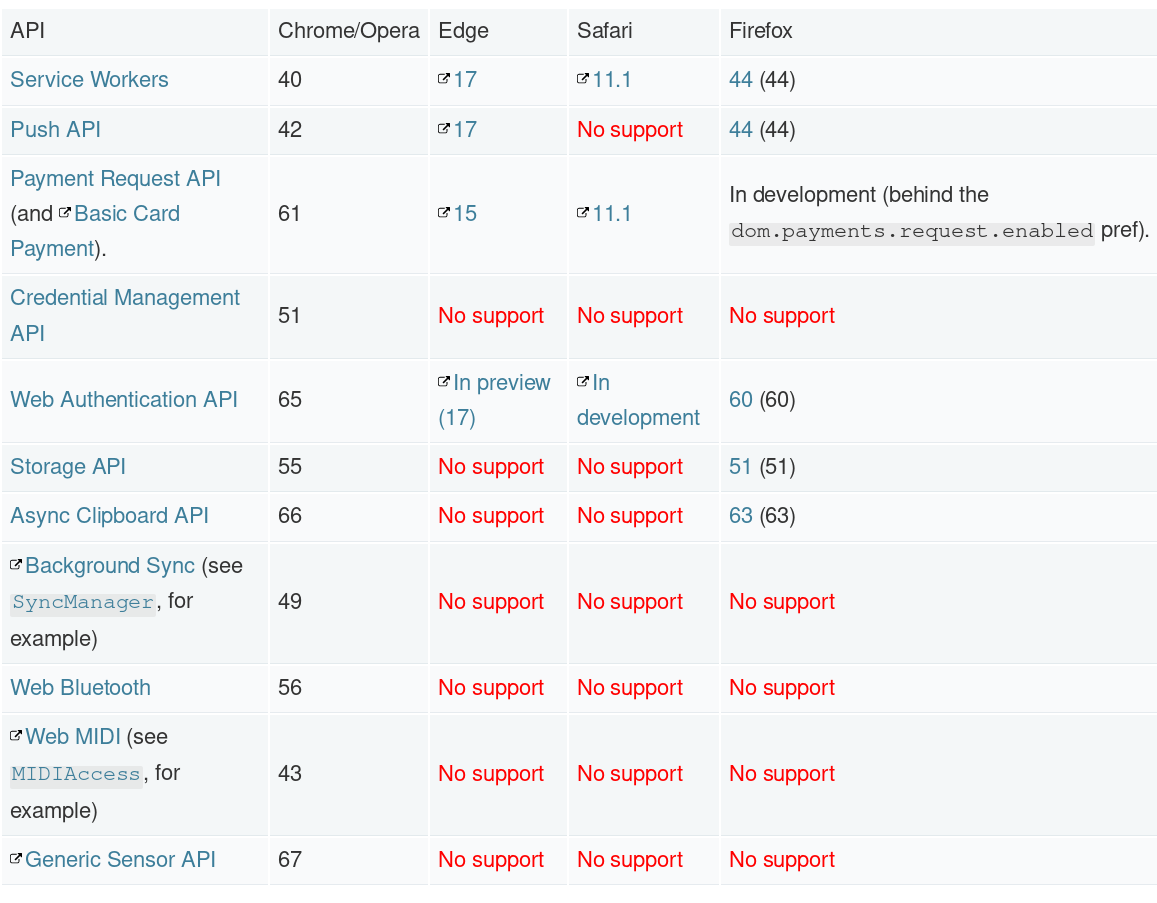

Many web servers and providers now have safe defaults, but always verify
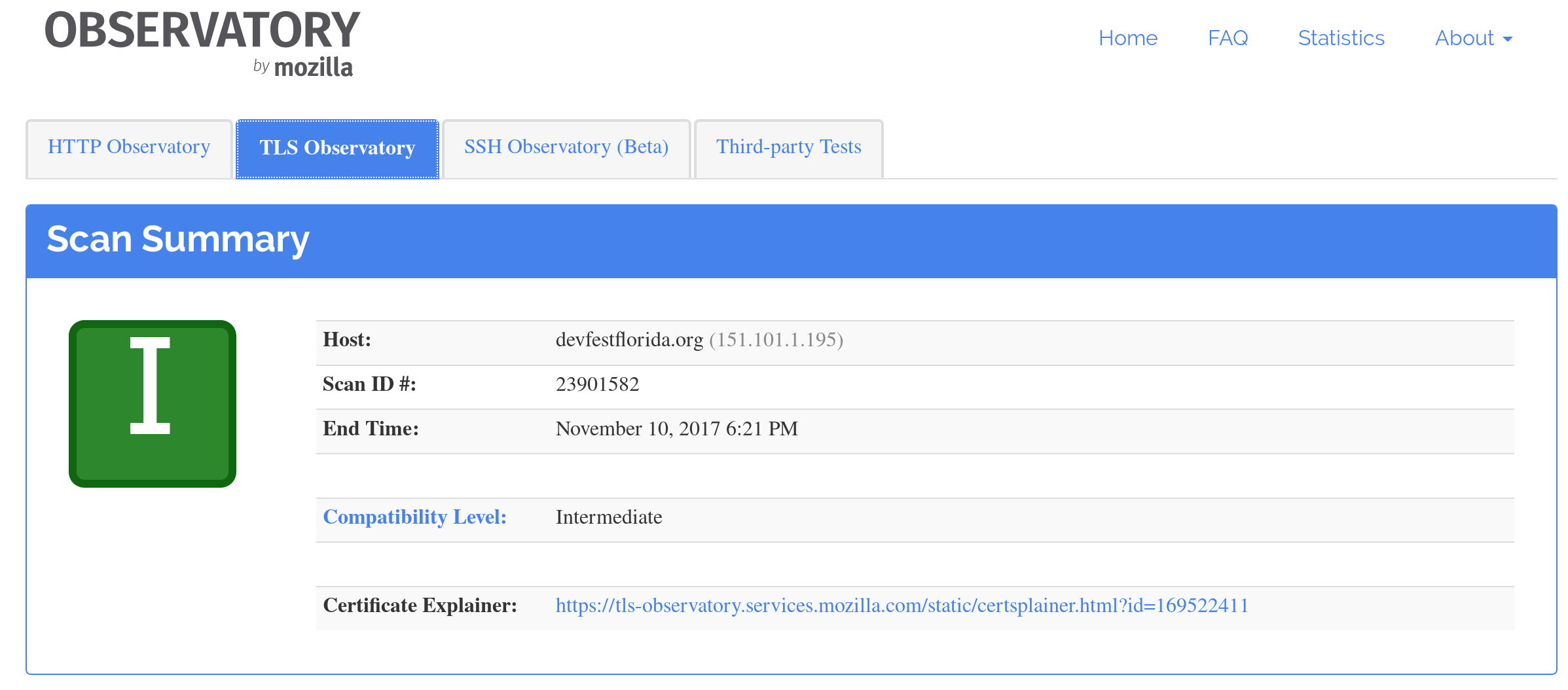
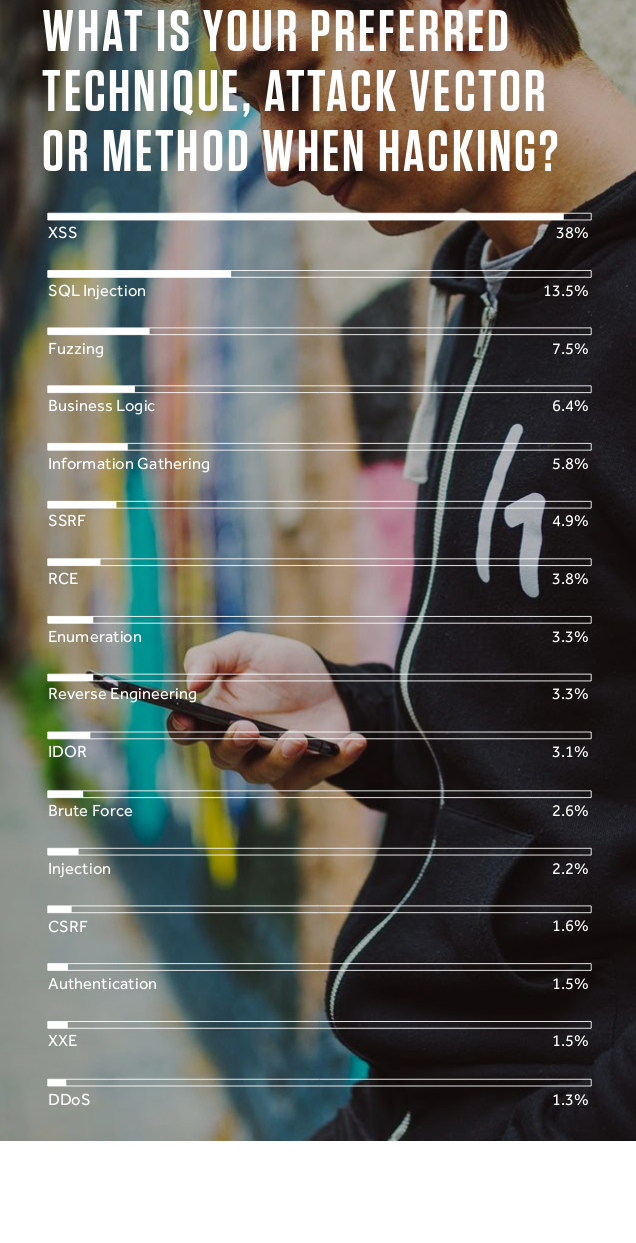
Hacker's favorite way to blowing up your webapps since....
pretty much forever.
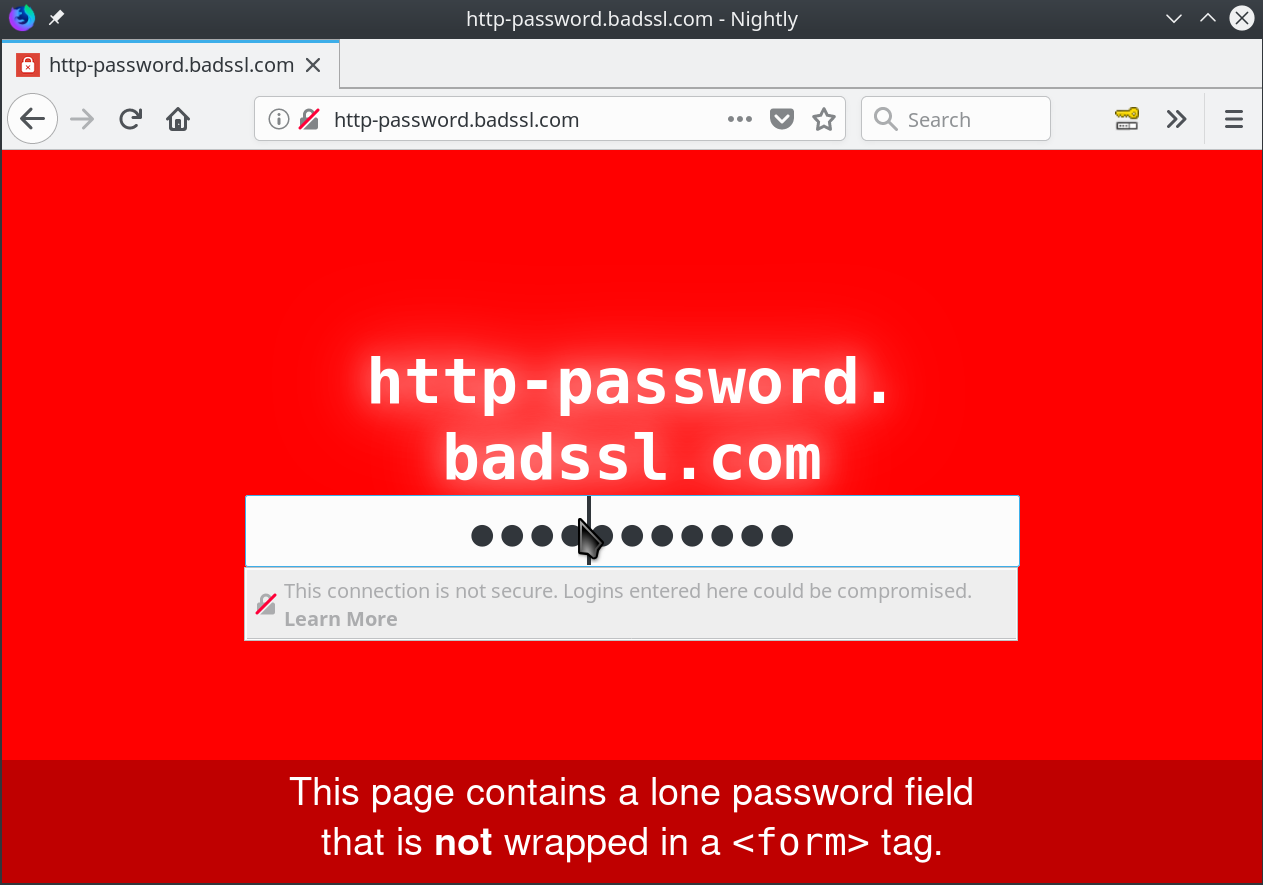
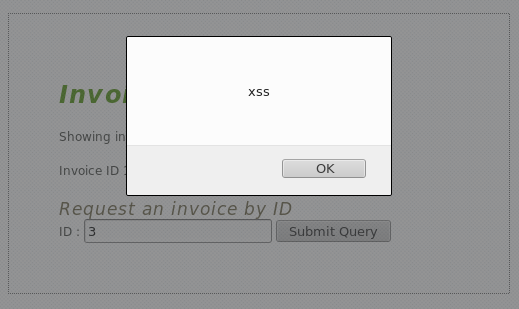
Cross-site scripting (XSS) is a security exploit which allows an attacker to inject into a website malicious client-side code. This code is executed by the victims and lets the attackers bypass access controls and impersonate users.
<script type='text/javascript'>alert('xss');</script>
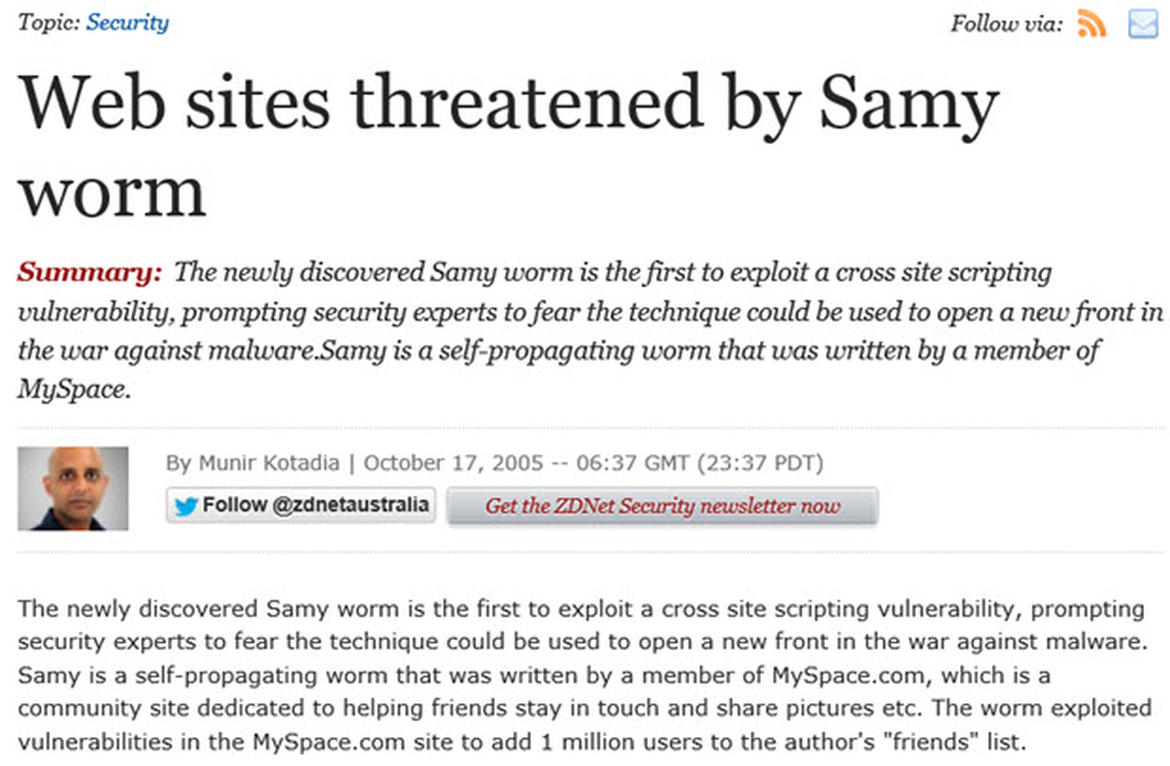
BACKGROUND: url('java
script:eval(document.all.mycode.expr)')"
expr="var B=String.fromCharCode(34);var A=String.fromCharCode(39);function g(){
var C;try{var D=document.body.createTextRange();C=D.htmlText}catch(e){}if(C){
return C}else{return eval('document.body.inne'+'rHTML')}}function
getData(AU){M=getFromURL(AU,'friendID');L=getFromURL(AU,'Mytoken')}function
getQueryParams(){var E=document.location.search;var F=E.substring(1,E.length).split('&');
var AS=new Array();for(var O=0;OF.length;O++){var I=F[O].split('=');AS[I[0]]=I[1]}return AS}
var J;var AS=getQueryParams();var L=AS['Mytoken'];var M=AS['friendID'];
if(location.hostname=='profile.myspace.com'){document.location='http://www.myspace.com'+
location.pathname+location.search}else{if(!M){getData(g())}main()}function getClientFID(){
Content-Security-Policy: default-src *; object-src 'none'
Disable the use of unsafe inline/eval,
allow everything else except plugin execution.
func setResponseHeaders() Middleware {
return func(h http.Handler) http.Handler {
return http.HandlerFunc(func(w http.ResponseWriter, r *http.Request) {
w.Header().Add("Content-Security-Policy",
"default-src *; object-src 'none'")
w.Header().Add("X-XSS-Protection",
"1; mode=block")
h.ServeHTTP(w, r)
})
}
}
You need to return the CSP header on every HTTP response.

This is easy: DON'T REFLECT IT ON YOUR MAIN ORIGIN!
Put user generated data on a separate domain that doesn't have cookies, and insert it on your main site with an iFrame.
This prevents UGC from having access to the origin.
This is (partly) why Facebook puts user images on "fbcdn.net"
Don't store user passwords, don't end up on this list.
Even with SSO/OIDC, put your admin panels behind a VPN. It will save you the day a bug bypasses your auth layer.
Breaking news: you're probably pulling half the internet in your webapp at every build.
The Jakarta Multipart parser in Apache Struts 2 2.3.x before 2.3.32 and 2.5.x before 2.5.10.1 has incorrect exception handling and error-message generation during file-upload attempts, which allows remote attackers to execute arbitrary commands via a crafted Content-Type, Content-Disposition, or Content-Length HTTP header, as exploited in the wild in March 2017 with a Content-Type header containing a #cmd= string.
What happens when an attacker gains access to merging patches to your application?
$ ./get_branch_protections.py --repo autograph mozilla-services
INFO: Finished gathering branch protection data (calls remaining 3379).
$ ./report_branch_status.py --header mozilla-services.db.json |column -t -s ','
| name | mfa | protected | restricted | enforcement | signed |
|---|---|---|---|---|---|
| autograph | True | True | True | True | True |
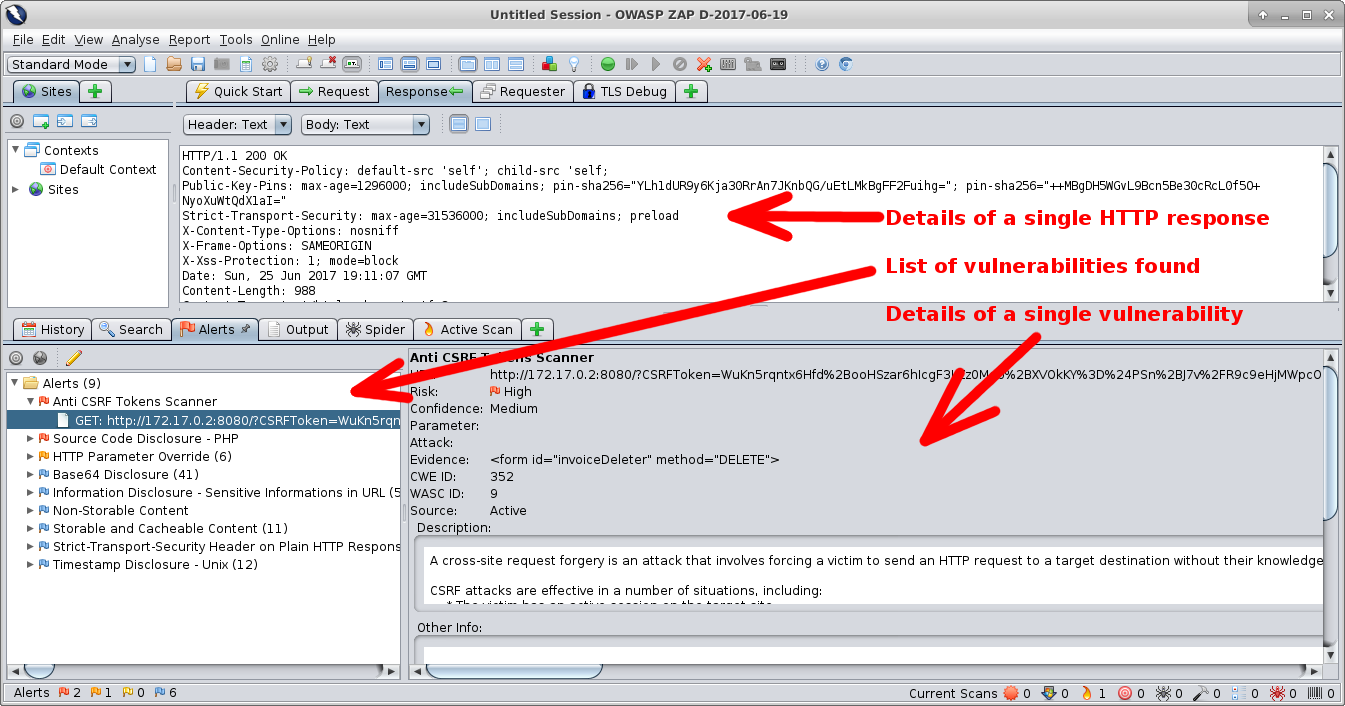
Four main types of security tests:
Automated tools that spider your website and apply series of tests to each resource discovered.
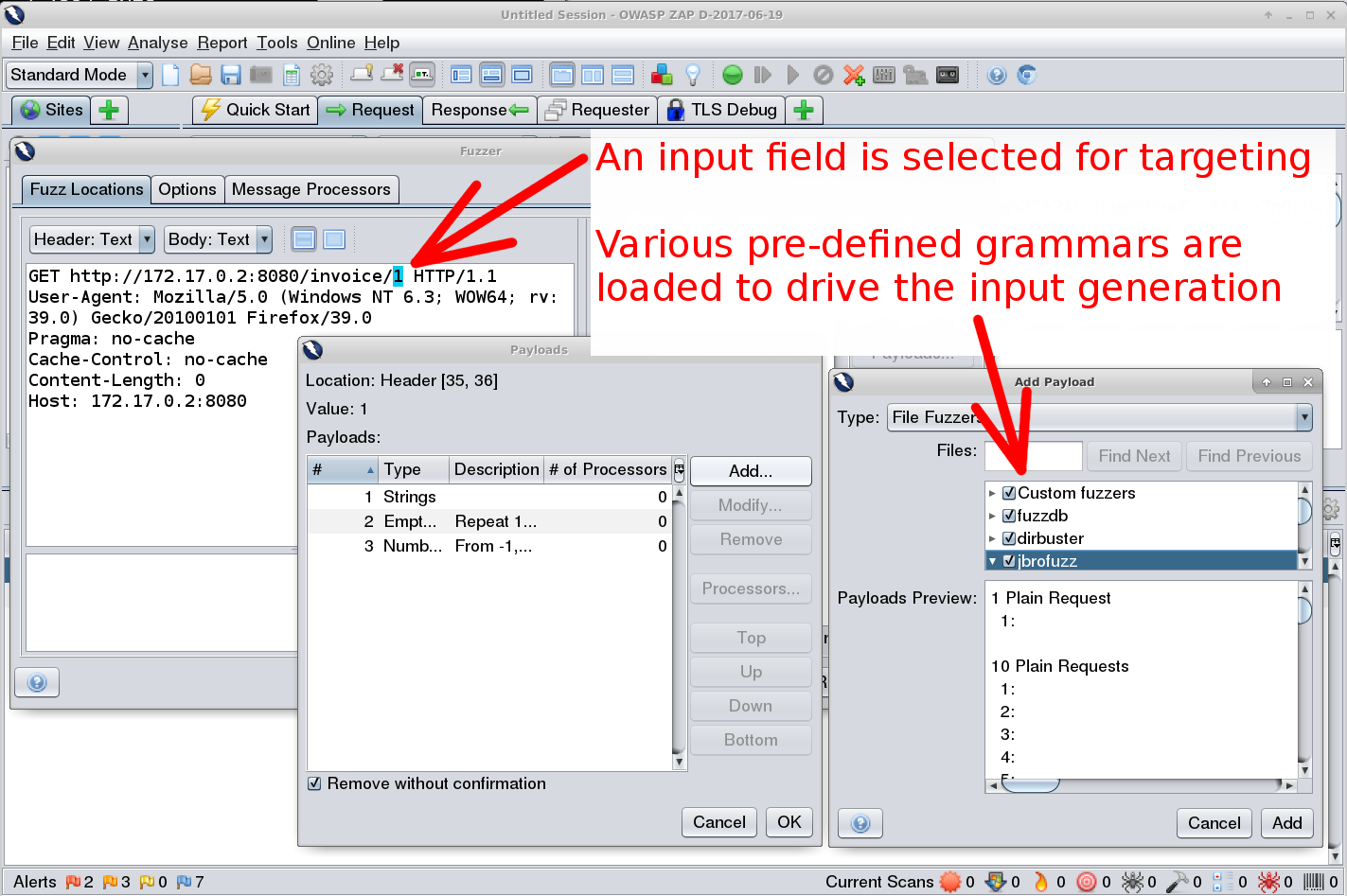
Inject junk into the interfaces of an app to make it crash.
$ bandit -r src/github.com/Kinto/kinto
Severity: High Confidence: High
Location: src/github.com/Kinto/kinto/kinto/plugins/accounts/scripts.py:36
>> Issue: [B322:blacklist] The input method in Python 2 will read from
standard input, evaluate and run the resulting string as python source
code. This is similar, though in many ways worse, then using eval.
On Python 2, use raw_input instead, input is safe in Python 3.
35 print('Username should match {0!r}, please try again.'.format(validator.regexp))
36 username = input('Username: ')
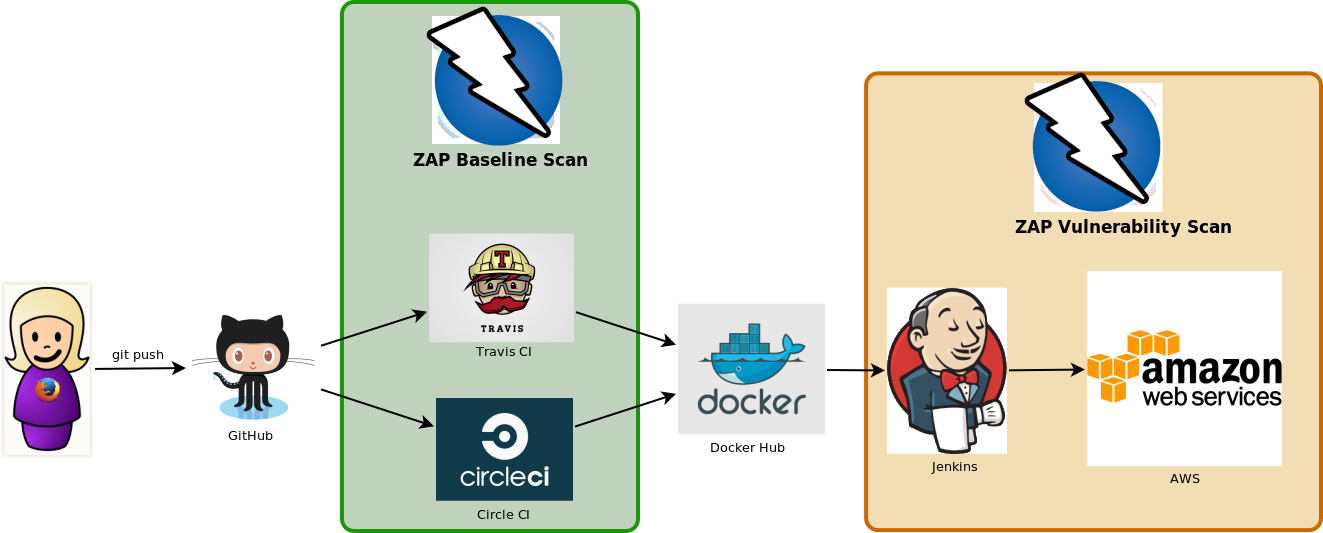
Don't deploy to prod unless the security tests pass in dev.
test:
- run myapp
background: true
# pull down the ZAP docker container
- docker pull owasp/zap2docker-weekly
# Run ZAP against the application
- docker run -t owasp/zap2docker-weekly zap-baseline.py \
-t http://myapp:8080/
PASS: Absence of Anti-CSRF Tokens [40014]
WARN: Web Browser XSS Protection Not Enabled [10016] x 3
http://172.17.0.2:8080/
http://172.17.0.2:8080//robots.txt
http://172.17.0.2:8080//sitemap.xml
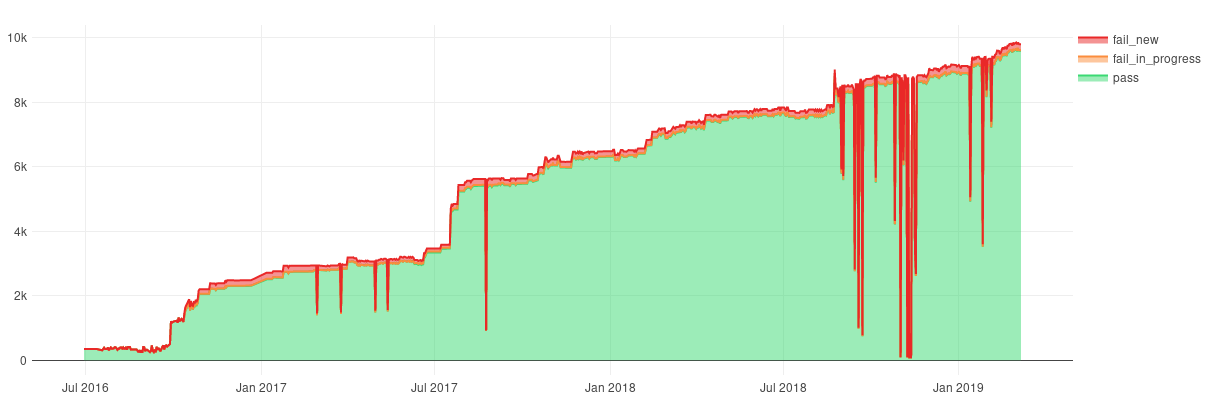
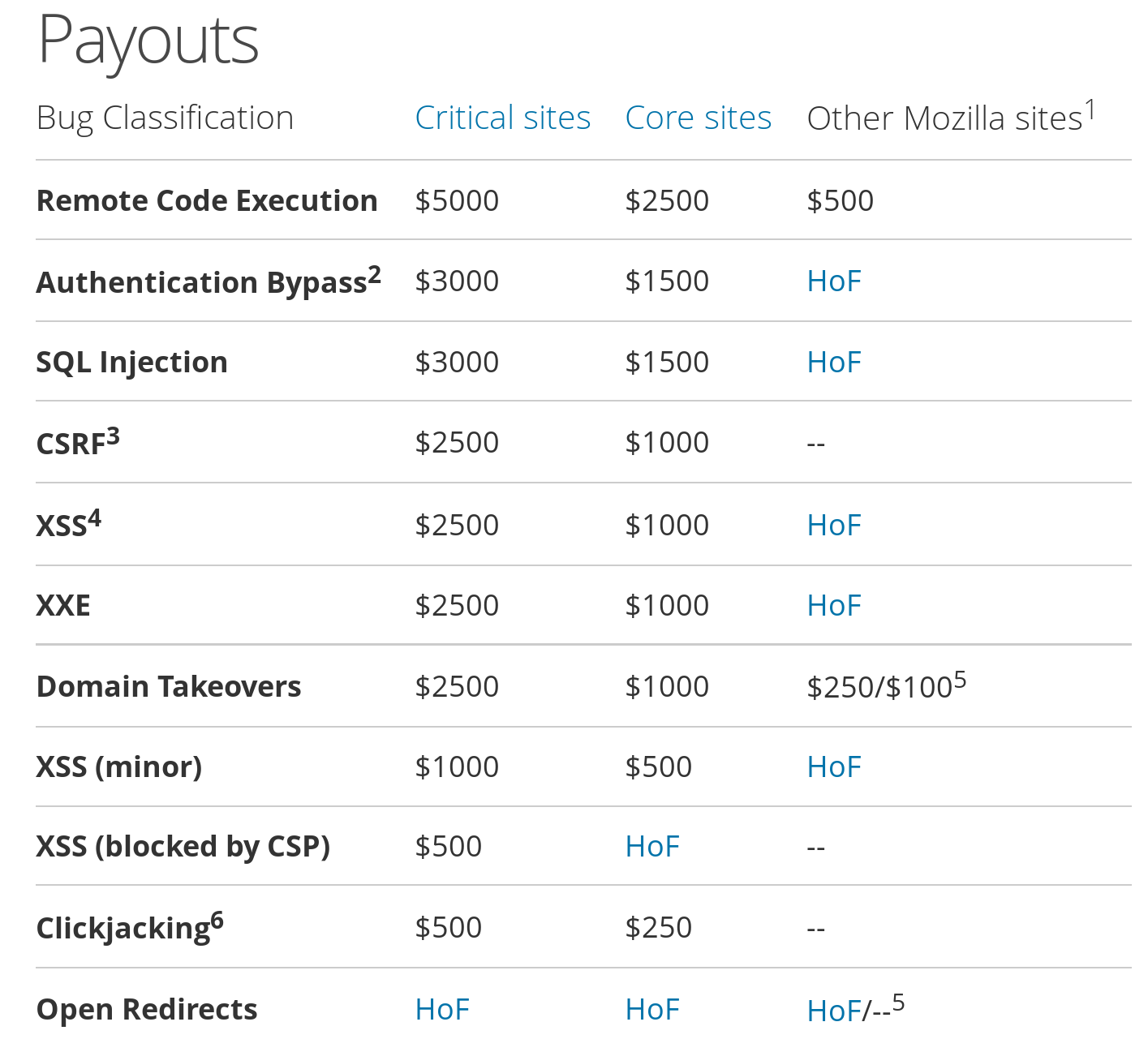
As soon as you have the budget, hire specialists to audit your website. Ideally, make that report public too.
Unless you're a big shop, it's much safer to outsource:
Heroku, AWS ElasticBeanstalk, Google
Cloud, etc.
|
 |
securing-devops.com |